I've mentioned in the past that I use renovate and dependabot to manage package updates for my repositories but sometimes though the build is good, the package update breaks my local development environment or doesn't follow my preferred practice. Since we get 2000 GitHub Action minutes for free on a personal account (and I have paid for minutes on some of my organisation accounts) I decide to use some of them for these sanity checks.
Yarn Package Deduplication
I have a preference to dedupe my packages and ensure that I have the highest version of each package that is possible. I do this so that when I am taking security updates I have found it is quicker to adopt these updates when my packages are already deduplicated. Usually renovate does a good job of deduplication (dependabot less so) but occasionally it doesn't dedupe the packages and I have to do this manually, but only if I know/recognise that this is required. Yarn v3 has a command for this yarn dedupe (for Yarn v1 I use the yarn-deduplicate package).
The GitHub Action for this looks like this
jobs:
yarn:
name: check yarn
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Setup Nodejs
uses: actions/setup-node@v3
with:
node-version: 18.x
cache: "yarn"
- run: yarn install --immutable
- run: yarn dedupe --checkUsing this action I can ensure that the package.json and the yarn.lock file are in sync and that there are no packages that can be deduped.
Validate .tool-versions
Just recently I took a renovate update that was to upgrade to the latest version of node 18 and as part of the that update it updated my .tool-versions. However the version of node being upgraded to wasn't yet available via the asdf tooling; the irony of this update breaking my developer experience is not lost on me. Whilst researching how to build my own step/action to install asdf and then install the tools to check their availability, I lucked upon an action that already does what I needed and so I plugged that in.
The GitHub Action for this looks something like this
jobs:
asdf:
name: check asdf
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- name: Install asdf & tools
uses: asdf-vm/actions/install@v3Once these sanity check steps are wired into the branch any failures of these steps will highlight in the PR and in the case of renovate stop any auto merges that have broken the build.
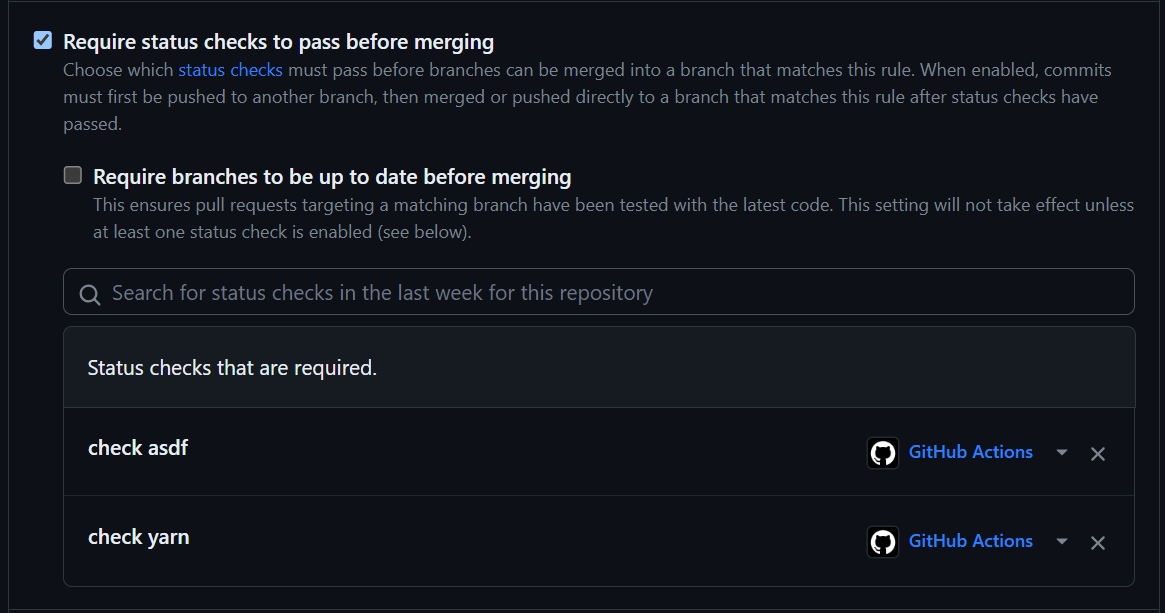
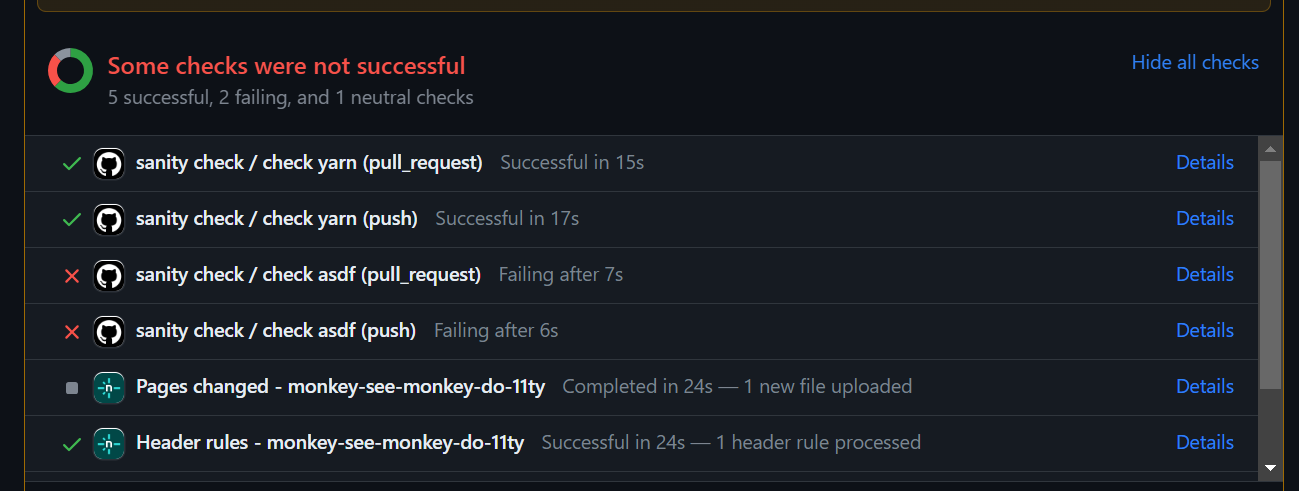
Though, I have shown the jobs as separate actions for the above examples it is more efficient (reduced GitHub Action minutes) to merge them together and run them as one.
As always, your feedback is welcomed and appreciated.
Photo by Bernard Hermant on Unsplash

